Data communications in business are vulnerable to malicious attacks, so it’s important to take the necessary steps to protect your data. Without the right security protocols in place, you may be putting your company’s sensitive information at risk. From encryption to using HTTPS, here are six steps to secure data communications.
Contents
1. Implement Encryption
Encryption is a key component of data security. It is the process of encoding data so that it can be read only by someone with the right key or password. Encryption is an essential element of most secure communication protocols and can be used both over the internet and within your own internal networks.
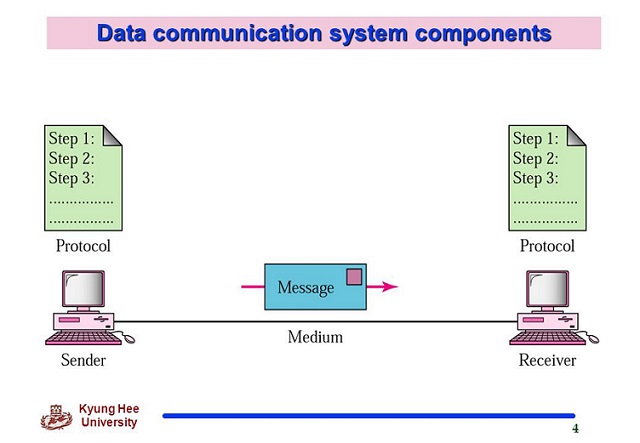
By using encryption to scramble your data, you make it much harder for malicious actors to access confidential information. Encryption solutions like AES and RSA are particularly effective options. AES is a symmetric-key algorithm that uses the same key for encryption and decryption, whereas RSA is an asymmetric-key algorithm that utilizes two different keys.
Read Also:
- European Markets Drop By 1%
- Alibaba’s New Measures to Prevent Sexual Harassment and Assault
- Microsoft’s Zero Percent Cut On Windows Apps Does Not Include Games
2. Use A Virtual Private Network (VPN)
A VPN is another effective tool for keeping data secure when communicating online. A VPN creates an encrypted tunnel between your device and the internet, making it impossible for malicious actors to intercept or access data transmitted over this secure connection.
VPNs are particularly important for employees who need to access sensitive information when working remotely. When choosing a VPN service, look for one that has strong encryption and a kill switch, which stops internet traffic if the VPN connection is lost.
3. Use Encrypted Network Protocols
Network protocols like Secure Shell (SSH) and Transport Layer Security (TLS) can be used to encrypt data as it is transmitted over networks, providing an additional layer of security. These protocols are designed to prevent eavesdropping and tampering, helping to ensure that only the intended recipient can access the data.
HTTPS is an encrypted version of the Hypertext Transfer Protocol (HTTP) used to securely transmit data across the web. It is essential for any website that deals with sensitive information such as credit card numbers or passwords. Web browsers will display a lock icon next to the URL when HTTPS is being used, indicating that the connection is secure.
4. Use Strong Authentication
Strong authentication is also an important part of securing data communications. Authentication ensures that only authorized users can access your systems and view confidential information. Common authentication methods include passwords, two-factor authentication (2FA), and biometric authentication, such as fingerprints or facial recognition.
Additionally, you can use IP address filtering and access control lists (ACLs) to further limit access. ACLs are used to grant access to certain users and deny access to others to prevent malicious actors from gaining unauthorized access to your systems. Using multiple layers of authentication can help ensure that only authorized users are accessing your data.
5. Use An Intrusion Detection System (IDS)
An Intrusion Detection System (IDS) is a tool used to detect and respond to malicious activity on your networks. It uses signatures, heuristics, and behavior-based algorithms to identify suspicious activity or potential threats.
An IDS can be used to monitor network traffic in real time, alerting you to any suspicious activity that could potentially compromise your data. This can help you take action quickly and prevent a security breach before it occurs.
6. Monitor Access Logs
Access logs track who is accessing your systems and when. By monitoring access logs, you can detect any suspicious activity or unauthorized access attempts. Whenever someone accesses your systems, their username and IP address should be recorded in the log.
You can also use access logs to identify potential weaknesses in your security protocols. For example, if an employee is accessing sensitive data more frequently than necessary, it could indicate that they are attempting to steal information or mishandling confidential data.
Regularly monitoring access logs is essential for keeping your data secure and minimizing the risk of a security breach.
Read Also:
- Career in IT
- Prepare Your Office for the Future
- Future of Enterprise Performance Management Solutions
Final Thoughts
Securing data communications is essential for protecting your business and avoiding costly security breaches. By using the tools and techniques discussed above, you can ensure that your data is always safe and secure. By implementing the right security protocols, you can protect your business from malicious actors and create a secure environment for your customers. After all, data security is essential for staying competitive in today’s digital landscape.